Another weakness was found in All in One SEO Pack. The newfound defenselessness can permit aggressors to assume full responsibility for a site utilizing a cross-site scripting weakness.
Cross-Site Scripting Exposure
These sorts of powerlessness are known as a cross-site scripting weakness (XSS).
It can for the most part include an undermined input interface. So anyplace that a client can include and transfer substance, pictures or contents should be “sterilized” so as to keep malignant contents from being transferred.
In this way, the common section focuses can be remarks and structures. In any case, these sorts of vulnerabilities can likewise influence zones of the site that are walled off from non-enrolled clients.
Recommendation – Pinterest Upgrades Its Algorithm To Display More Content Types In Home Feed
The powerlessness influencing All in One SEO Pack influences a zone of the site that requires a client to have posting benefits.
Along these lines, it’s portrayed as a medium level powerlessness.
Is Compact SEO Pack Weak?
Truly, All in One SEO Pack (versions 3.6.1 and under) is powerless against an XSS exploit. This specific endeavor influences an info region that isn’t disinfected.
The influenced zone is the SEO title and SEO depiction fields, where a sign in client with posting benefits can transfer malignant contents to increase authoritative access, assume control over the site, or to taint site guests. As terrible as that sounds, this is a medium level seriousness weakness since it requires a programmer to get to sign in qualifications of an enlisted client with posting benefits. So as to achieve that the programmer may need to utilize social designing stunts to take the certifications or exploit helplessness in another module or subject.
According to WordFence
“Due to the JavaScript being executed whenever a user accessed the ‘all posts’ page, this vulnerability would be a prime target for attackers that are able to gain access to an account that allows them to post content.
Since Contributors must submit all posts for review by an Administrator or Editor, a malicious Contributor could be confident that a higher privileged user would access the ‘all posts’ area to review any pending posts.
If the malicious JavaScript was executed in an Administrator’s browser, it could be used to inject backdoors or add new administrative users and take over a site.”
How it came into notice?
How Vulnerability Security scientists at WordFence found the powerlessness in All in One SEO Pack on July 10, 2020, and quickly advised the distributors of the module. The distributors set to chip away at refreshing the powerlessness and discharged a fix on July 15, 2020, after five days. Premium clients of the WordFence Security Plugin got a firewall rule update around the same time that the helplessness was found, July 10, 2020.
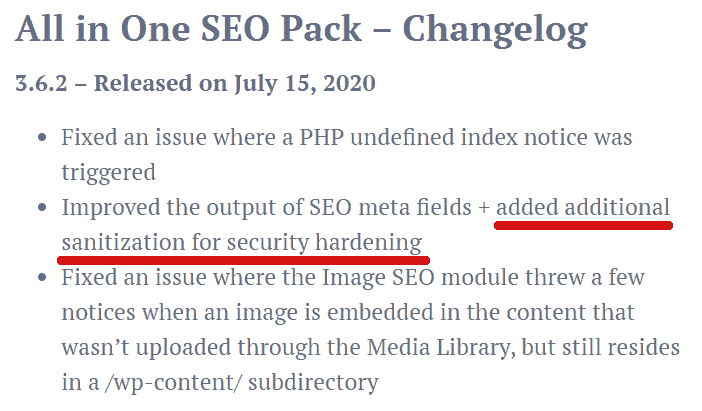
The update to All in One SEO Pack is accurately alluded to in their changelog:
“Improved the output of SEO meta fields + added additional sanitization for security hardening”
Updates
Each and every individual who utilizes All in One SEO Pack is urged to refresh their module to versions 3.6.2 right away. While this is appraised as a medium seriousness defenselessness it is as yet judicious to fix the module with the goal that it is sheltered.